Jan 09, 2025
Aris S.
11min Read

Being the most popular content management system (CMS), WordPress is a common target of cyber attacks. While the platform is safe, website owners must apply robust security practices to minimize the risks.
If you see signs of hacked WordPress, like unauthorized redirection or modified content, malware might be infecting your site. If not handled properly, this can lead to serious issues, including data loss and downtime.
In this tutorial, we will explain different methods of WordPress malware removal. You will learn how to do so manually, automatically, or using a third-party service so you can choose the one most suitable for your needs.
Download WordPress security checklist
Want to learn more about malware? Check our video tutorial to learn more about different types of malicious software and how to protect your website against them.

Before eliminating WordPress malware, make sure to complete the following tasks to prevent the attack from getting worse.
If you suspect your WordPress site is compromised, immediately restrict its access to prevent users from visiting it. Otherwise, the malware might spread to visitors’ devices or redirect them to phishing sites.
This step also ensures that only administrators resolve the issue, allowing you to track changes more easily in case of errors.
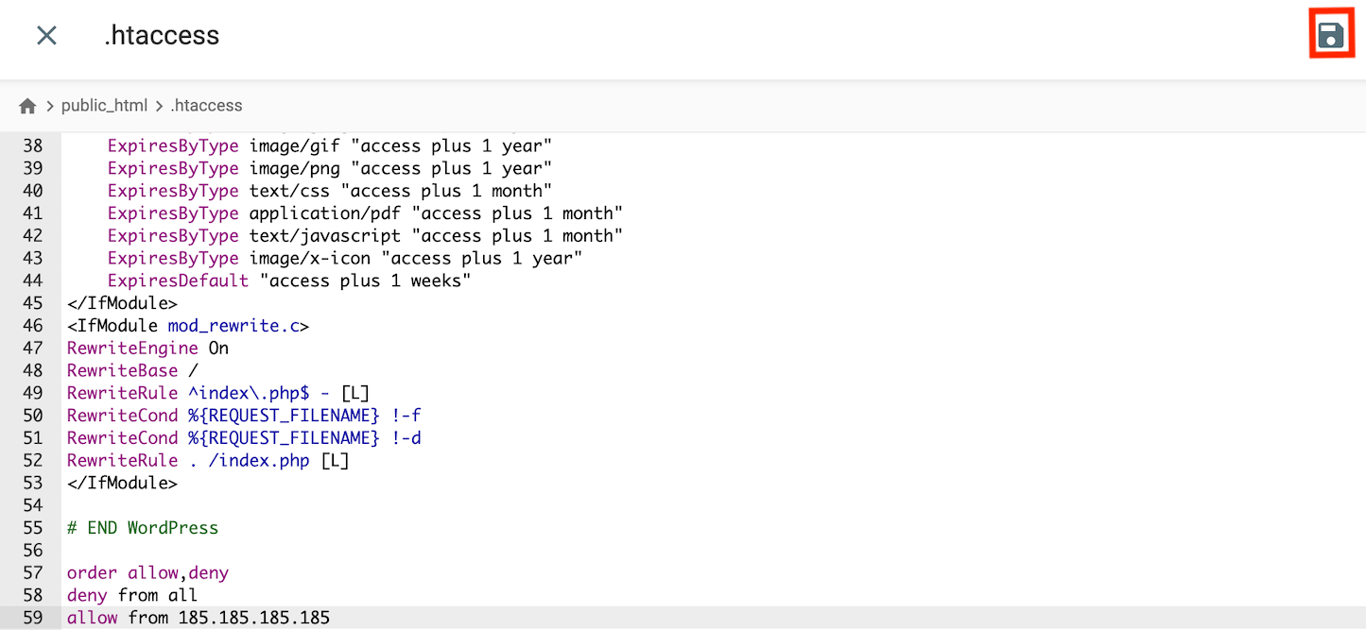
To restrict WordPress access, block all IP addresses except your computer’s via the .htaccess file. Here’s how to do so on the Hostinger hosting plan:
order allow,deny
deny from all
allow from [your_IP_address]
Before doing so, remember to set up a static IP address on your computer. Otherwise, you must update the .htaccess file periodically since the value will change.
Backing up your website files helps you pinpoint the malware infection more quickly. It lets you compare the data before and after the attack to distinguish the malicious code.
The steps of creating a WordPress backup differ depending on the web hosting company. For Hostinger users, follow these:
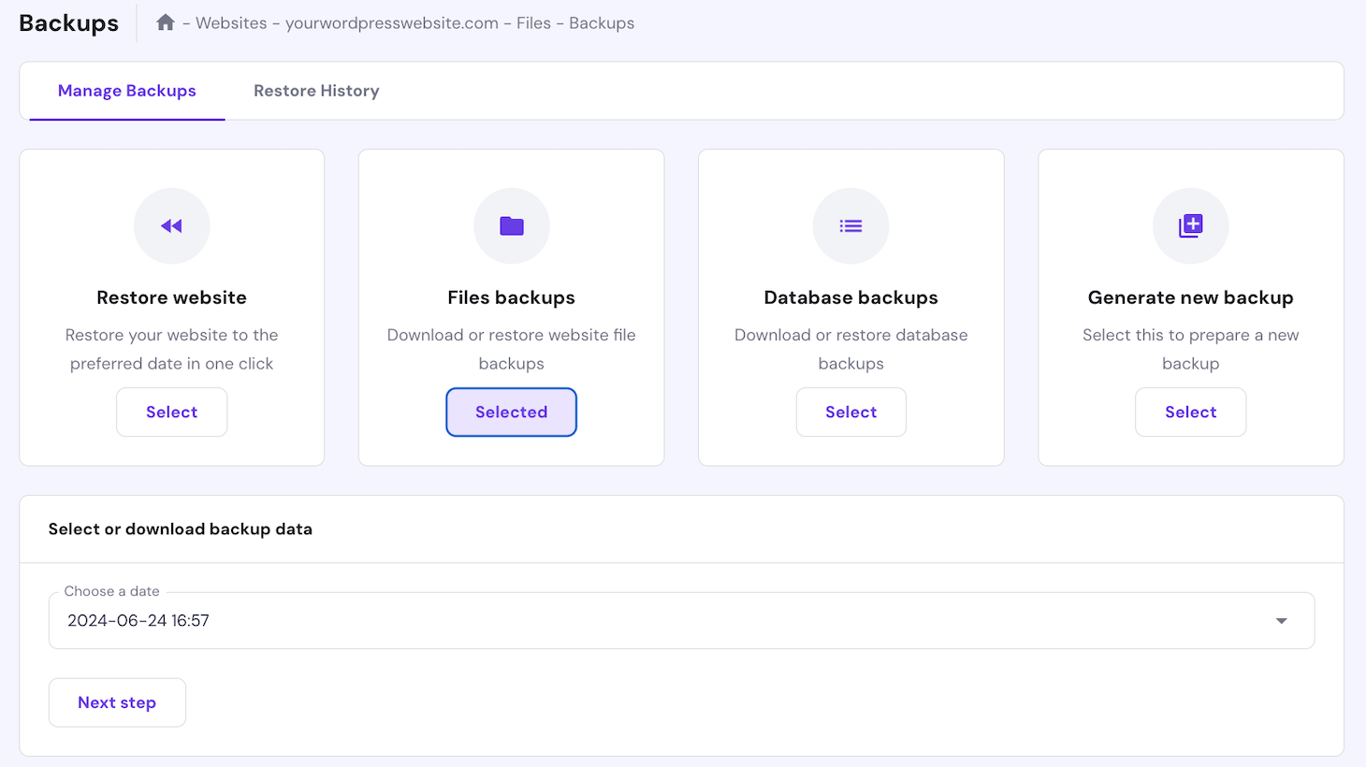
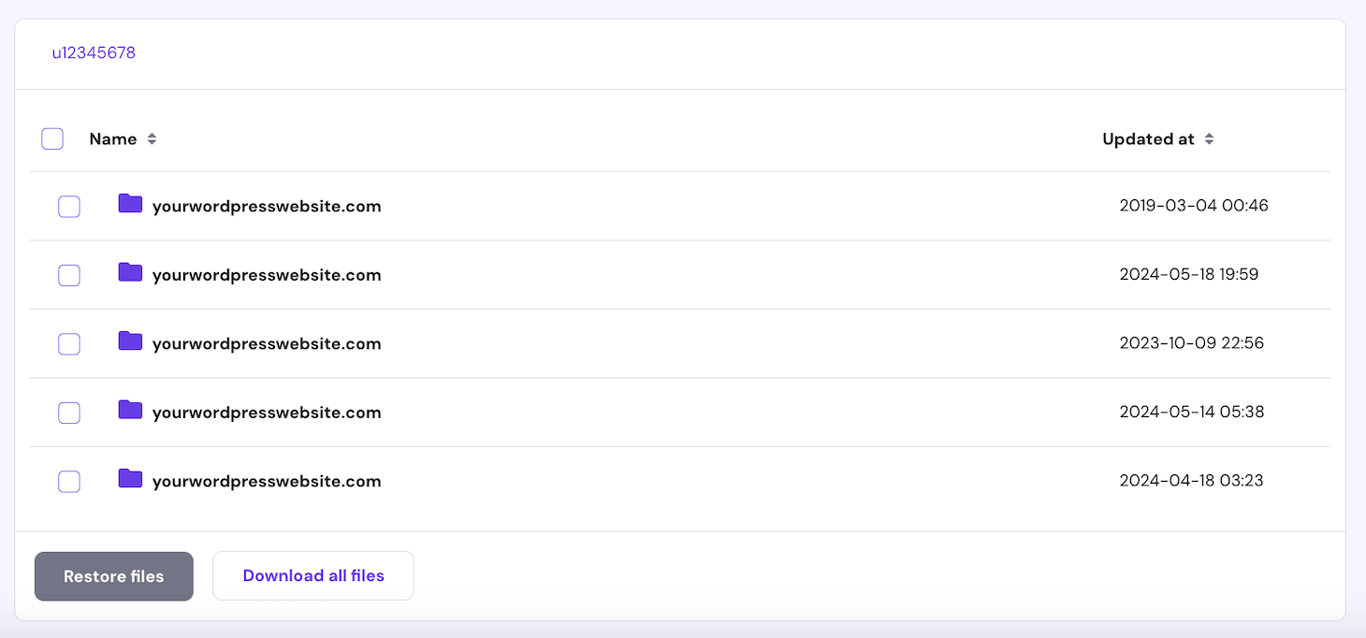
All Hostinger web hosting plans have automatic weekly backups to ensure you have an up-to-date recovery point.
However, not all web hosts offer the same feature, meaning you can’t download a backup if you haven’t created one manually. In this case, we recommend contacting your hosting provider to check if they have a copy of your website files.
Tracking recent modifications on your website helps you identify which file is infected with malware.
A simple way to do this is by checking the activity log. At Hostinger, you can do so via hPanel by going to Website Management → Performance → Analytics → Access Logs.
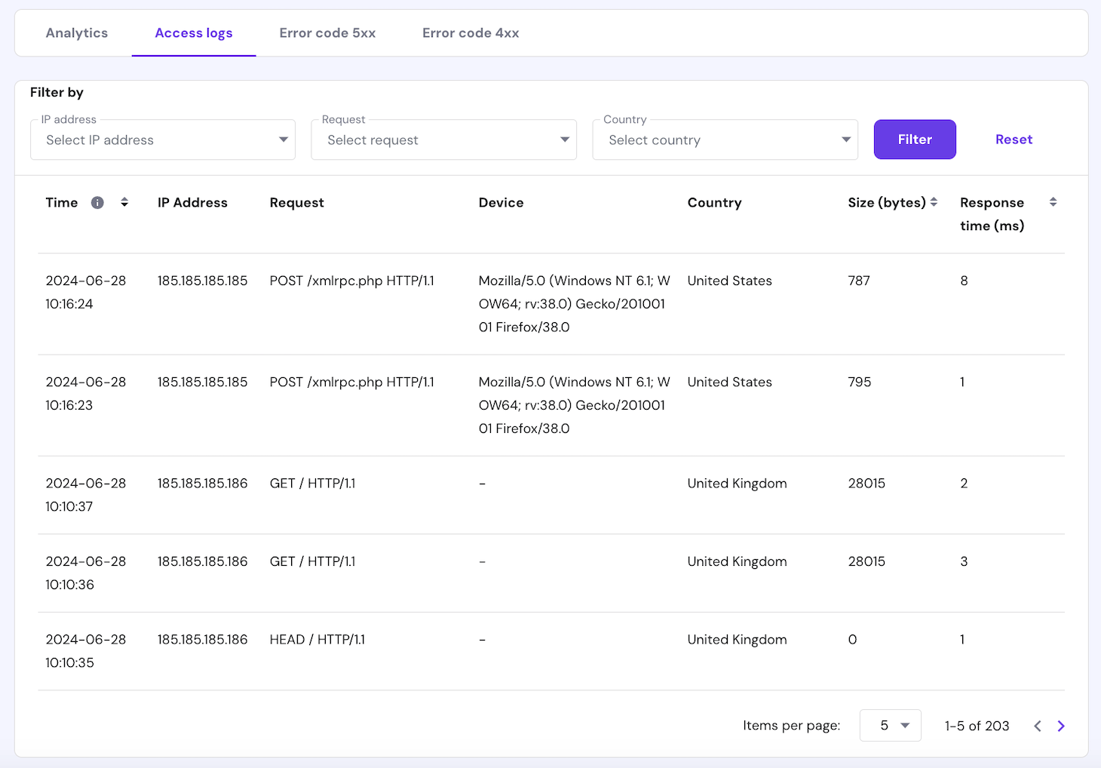
For a more detailed analysis, you can also list recently modified files using a command. To do so, connect to your WordPress server via SSH using Terminal or a client like PuTTY. Then, run the following:
find . -type f -name '*.file_extension' -ctime n
Replace file_extension with the actual file format you want to check, such as PHP or JS, which are common targets for malware attacks. n specifies the time span you wish to check as days. In this example, we will search for JavaScript files modified three days ago:
find . -type f -name '*.js' -ctime -3
Cybercriminals might use malware to steal WordPress administrators’ credentials. If your website is compromised, immediately change all passwords to slow down the attack.
We also recommend updating credentials on other platforms, including the WordPress database, hosting panel, and File Transfer Protocol (FTP) client. To minimize security threats, use a robust and unique password for each account.
To simplify the process, use a password generator tool like 1Password Strong Password Generator. In addition, store all your credentials in applications like NordPass or 1Password, which provides an encrypted vault to safeguard your login information.
In addition, change the WordPress salts to keep your new login details secure. You can reset salts and all admin passwords to a random string of characters by running the following command via SSH:
wp config shuffle-salts && wp user reset-password $(wp user list --role=administrator --field=ID)
Symlinks lets you create shortcuts that point to files or directories, providing multiple access points for a simpler management process.
However, cyber attackers can exploit compromised shortcuts to access important files or the root folder. To avoid this issue, unlock the symlink by running this command via SSH:
find . -type l -exec unlink {} \;After completing the WordPress malware removal steps, remember to recreate the symlink; otherwise, your website might not work correctly.
Outdated WordPress might have security vulnerabilities. Updating it ensures you apply the latest patch, minimizing the known attack surface for cybercriminals.
In addition to WordPress, make sure to update plugins and themes, as hackers can exploit them to gain access to your website. At Hostinger, hPanel has vulnerability detection that alerts you about compromised extensions.
Moreover, update your PHP version since this scripting language is susceptible to attacks like SQL injection and cross-scripting. You can also do so via hPanel by going to the website management menu → sidebar → Advanced → PHP configuration.
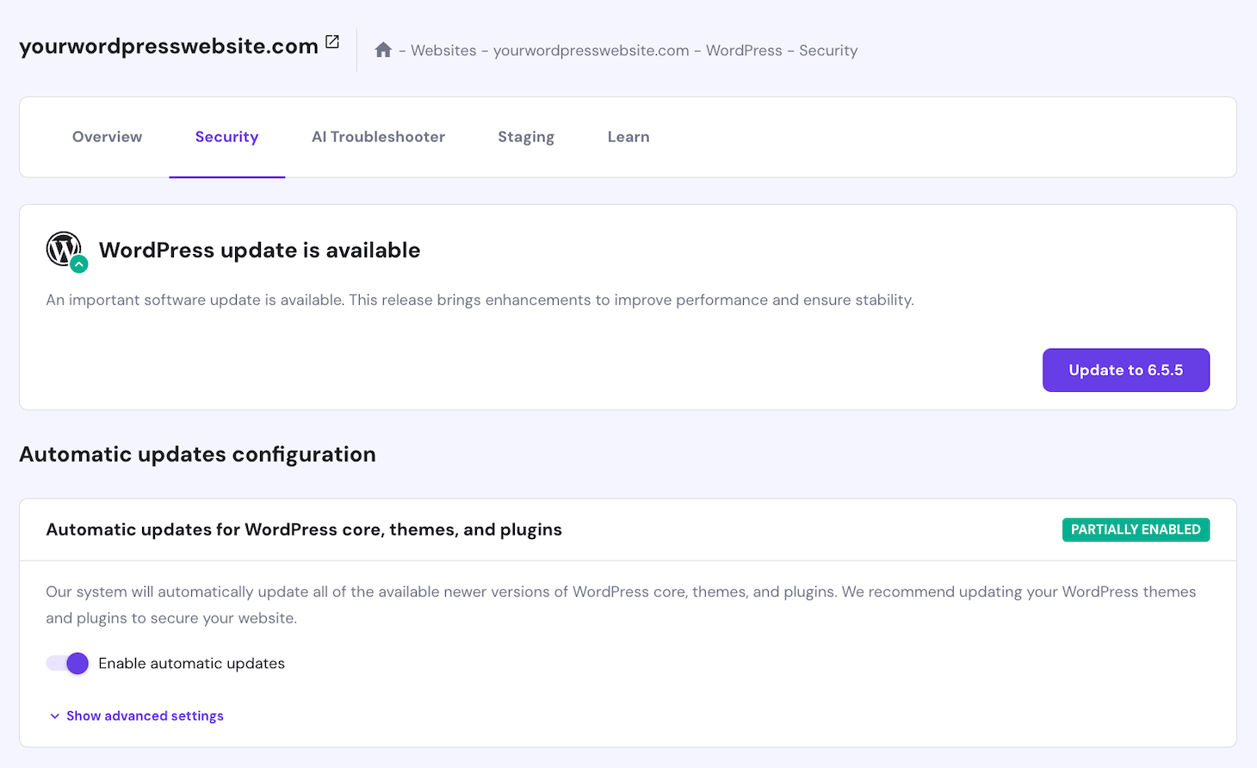
We also recommend enabling hPanel’s automatic update feature to ensure your WordPress installation, plugins, and themes use the latest security patches as soon as possible. Do so by going to the sidebar → WordPress → Security.
Unsupported plugins and themes are significant security risks as they don’t receive patches to remove any vulnerabilities. Always check when your extensions were last updated. If there have been no updates and activities in the development log in the past six months, it’s safer to uninstall the plugin or theme and look for an alternative.
Changing file permissions might expose sensitive data to the public, which cyber attackers can exploit to infect your website. Resetting access privileges prevents unauthorized parties from modifying essential data.
You can do so using an FTP client like FileZilla or hPanel’s File Manager. Ideally, set permissions for files to 644 and folders to 755. To learn what these values mean, check our chmod command tutorial.
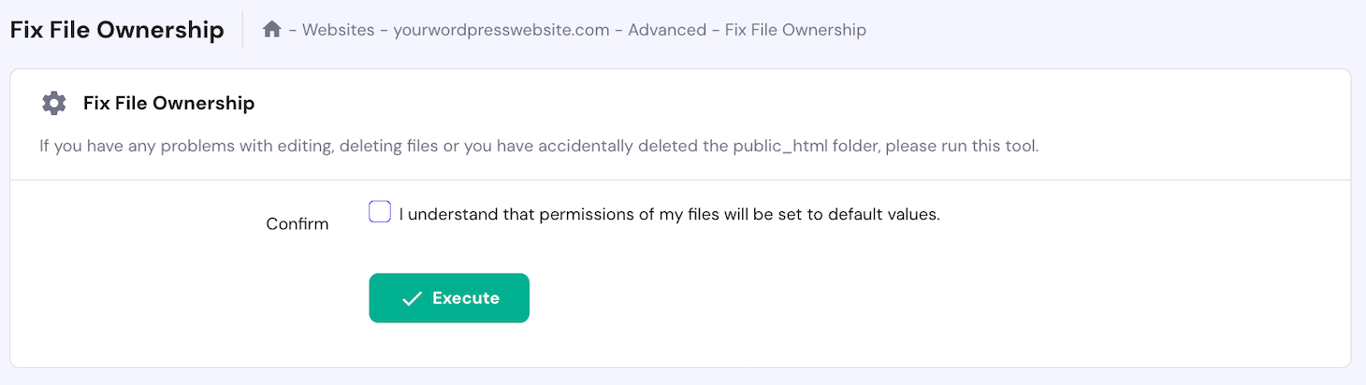
Alternatively, Hostinger users can reset all file permissions in a single click via hPanel. To do so, navigate to the website management menu → sidebar → Other → Fix File Ownership. Check the box and click Execute.
Malware in WordPress can also infect your personal computer when you access the infected website or download its files. Before cleaning it up, it is essential to check if your system is also compromised.
This step prevents the malware from spreading back into your website. You can clean up your computer using various antivirus software like Bitdefender and Norton.
Users with technical knowledge can manually remove malware from their WordPress sites. While this method can be complicated for beginners, it works across different hosts.
The first step to remove malware from WordPress is reinstalling the CMS’ core files. If you still have access to the admin dashboard, you can do so by navigating to the sidebar → Updates and clicking the Re-install Now button.
Otherwise, you reinstall WordPress using an FTP client or File Manager in hPanel. Here’s how to do so at Hostinger:
Alternatively, reinstall the core files using the WordPress command-line interface (WP-CLI). Before doing so, open File Manager and navigate to the public_html root directory.
Rename wp-admin and wp-include folders by right-clicking them and selecting Rename. Doing so will force WP-CLI to download new files, which is preferred since those folders might be compromised.
Once finished, connect to your website via SSH and run the following command. Replace 6.6 with your preferred WordPress version:
wp core download --version=6.6 --skip-content --force
Now, we have clean and infected WordPress files. Let’s compare them to check which item has the malicious code so we can remove them from the installation.
You can identify malware manually using the split window feature of your FTP client. However, it can be tedious since WordPress has a lot of files, especially if your website is complex.
Use commands to highlight disparities between your website code quickly. To do so, put the clean and infected WordPress files into two folders on your server. Then, run the following via SSH:
diff -r wordpress-clean/ wordpress-infected/ -x wp-content
You can also run a checksum via WP-CLI to verify the integrity of your website files. This process compares your WordPress core’s data block with the original one to identify unauthorized changes. Here’s the command:
wp core verify-checksums
You can also run a checksum on plugins. However, this often yields an error since the command only works for official WordPress extensions:
wp plugin verify-checksum
Remember that slight adjustments on your files can cause a checksum error. So, before running the command, ensure you have a fresh copy of the core WordPress files.
Cybercriminals often exploit PHP files to inject your WordPress with malicious code. Removing them from the Uploads folder can help close the hackers’ entry points, minimizing the risk of further attacks.
To do so, open your WordPress installation folder using an FTP client or Hostinger File Manager. Then, navigate to public_html → Uploads, and remove all the files.
In File Manager, you can delete files in bulk by clicking the checkmark icon at the top right, selecting the files to remove, and choosing the action.
You can also delete all PHP files within the Uploads folder using commands via SSH:
cd public_html/uploads/ && rm *.php
However, we recommend checking the Upload folder’s content first since the command will wipe all the files, potentially removing a critical item. You can quickly list PHP items by running the following:
find . -name ".php"
In order to create a backdoor, cybercriminals often inject harmful code into PHP files in your WordPress installation, themes, and plugins. You can’t simply remove these items since they are essential for website functionality.
The target scripts for hidden backdoors vary, but the most common ones include wp-config.php and functions.php. To create an entry point, hackers typically insert PHP functions like base64, exec, move_uploaded_file, and str_rot13.
To quickly identify potentially compromised PHP files, check if those PHP functions exist on your website. Here’s the command:
find . -type f -name '*.php' | xargs egrep -i "(mail|fsockopen|pfsockopen|stream\_socket\_client|exec|system|passthru|eval|base64_decode) *)"
Remove any additional scripts in the compromised files. For reference, you can set up a new staging WordPress site to see the original code.
We also recommend checking image and iframe files since hackers might include a backdoor when uploading them to your website. Here are the commands:
find wp-content/uploads -type f -iname '*.jpg' | xargs grep -i php
find . -type f -name '*.php'| grep -i '<iframe'
Important! Some themes and plugins use these PHP functions to work correctly. Check the extensions after cleaning them to ensure you don’t remove any essential functions.
In addition to the core files, clean malware in your WordPress database by removing suspicious scripts. There are two methods to do so – using WP-CLI commands or manually inspecting the backup.
To search for malicious scripts in your SQL database, connect to the website’s server via SSH and run the following:
wp db search "<script"
This command will output all entries with the <script tag from your SQL database. Don’t remove suspicious entries yet since we will use them to help check potentially compromised posts in the next step.
To make the process more efficient, you can also search for scripts containing JavaScript functions that cybercriminals often exploit. In this example, we are checking for eval(), atob(), and fromCharCode():
wp db search '(<script|eval\(|atob|fromCharCode)' --regex
To do so manually, open the SQL database backup we created earlier and search for suspicious scripts. To simplify the task, we recommend using a code editor with a highlighter and a search feature like Sublime or Visual Studio Code.
Cybercriminals might exploit input functionality on your WordPress posts, pages, and comment section to insert malicious content. Check recent changes on them to catch suspicious modifications.
To review post or page revisions, open your WordPress dashboard and edit the content you want to check. Open the Settings sidebar, click the three-dot icon, and select Revisions. If you can’t find the option, there hasn’t been any change since publishing.
Such malicious content might only be visible using the code editor. To check for these, click the three-dot icon and select Code Editor.
For comments, check the history by going to the WordPress dashboard → sidebar → Comments. Remove unwanted entries by hovering over the comment and clicking Trash.
Now, check the scripts obtained from the previous step to identify which area of your website is compromised. This step is crucial since changes in posts, pages, or comments will write new entries in your database tables.
To do so, open the database backup using a text editor and manually delete unwanted scripts from the entry.
After you delete malware and suspicious code from WordPress, let’s check if unauthorized accounts exist on your website. Cybercriminals often create new admin users to modify your website or access important data from the inside.
To do so, open your WordPress dashboard and go to sidebar → Users → All Users. From the list, check if there are new, suspicious admin accounts. If you found one, delete it by checking the box next to the name and selecting Delete from the Bulk actions menu.
Also, review other accounts’ roles to ensure only authorized users can access critical files. Change their roles by checking the box next to their name and selecting a new title from the Change the role to… menu.
You can also use WP-CLI to check users in more detail. For example, run the following to list all accounts sorted by their creation date:
wp user list --fields=ID,user_login,user_registered --orderby=user_registered --order=ASC --format=table --debug
To protect visitors, Google will automatically flag your site if it gets hacked or infected with malware. After cleaning malicious software, remember to remove your website URL from Google’s blocklist.
You can do so via your Google Search Console admin dashboard. Open the Security & Manual Actions and click the Security issues tab. Select I have fixed these issues → Request a review to ask Google to re-index your WordPress site.
Note that the process can take a few days. We recommend doing it immediately since the longer Google blocks your website, the more it harms search engine optimization (SEO) and your website reputation.
A more straightforward solution to remove malicious software from WordPress is to use malware scanner plugins like WordFence. With a few clicks, you can identify compromised areas of your website, allowing you to clean them up more quickly.
However, cyber attackers might restrict your access to the WordPress admin dashboard, preventing you from installing and using the tool. In this case, use other methods or ask your web host for assistance.
If you use Hostinger Managed WordPress hosting, you can run a malware scan via hPanel when the admin dashboard is inaccessible. To do so, navigate to the website management screen → sidebar → Security → Malware Scanner.
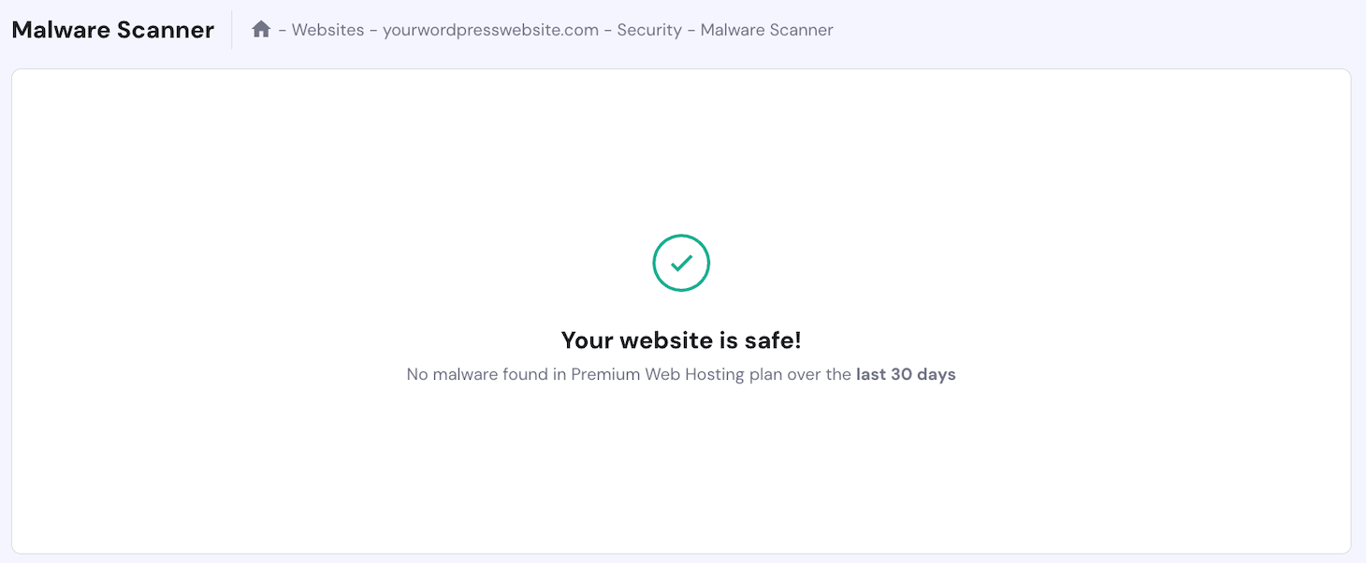
From this menu, you can see a summary of the latest scan, including the amount of malware discovered, removed, and cleaned. Otherwise, you will see a message stating that your website is safe.
Note that this tool will automatically scan and remove malware from WordPress, so you don’t need to clean your website manually.

If you encounter difficulties when removing malware from your WordPress website, consider using a professional service. We also recommend doing so when dealing with complex issues.
A professional can properly clean malware on your website, ensuring no malicious scripts or backdoors remain. Hiring experts also prevents you from deleting important files during the removal process to maintain functionality.
Several development agencies offer WordPress malware removal services. However, if you are on a tight budget, look for freelancers on websites like Upwork and Fiverr.
When looking for freelance services, write a clear job description to find a suitable candidate more quickly. After getting applicants, review their portfolios to determine if their expertise is suitable for your recovery task.
Checking reviews is also essential to determine if the freelancer can work quickly since malware infection requires immediate fixes. If needed, you can also ask other developers or friends for recommendations for similar services.
Malware infection is a common cyber attack on WordPress that can cause serious damage. However, you can quickly clean your site from this malicious software using the right tools and methods.
Before cleaning up the malware, restrict your WordPress access and download all the available backups to avoid further damage. Then, reinstall the WordPress core via hPanel or download the components using WP-CLI through SSH.
Then, delete malicious scripts on your PHP files, SQL databases, and posts. After you remove malware from WordPress, remove suspicious admin users and request Google to unflag your website via the search console.
You can also remove malicious software from WordPress using plugins like Wordfence or Hostinger’s built-in malware scanner in hPanel. If you find the issue too complex, consider hiring professionals from agencies or freelance websites.
All of the tutorial content on this website is subject to Hostinger's rigorous editorial standards and values.