Important Information Regarding Phishing Emails Using Hostinger Name

We have received an increased number of phishing reports from our customers. They are receiving malicious emails which are impersonating our services and trying to steal sensitive information.
This is an example of a reported phishing email:
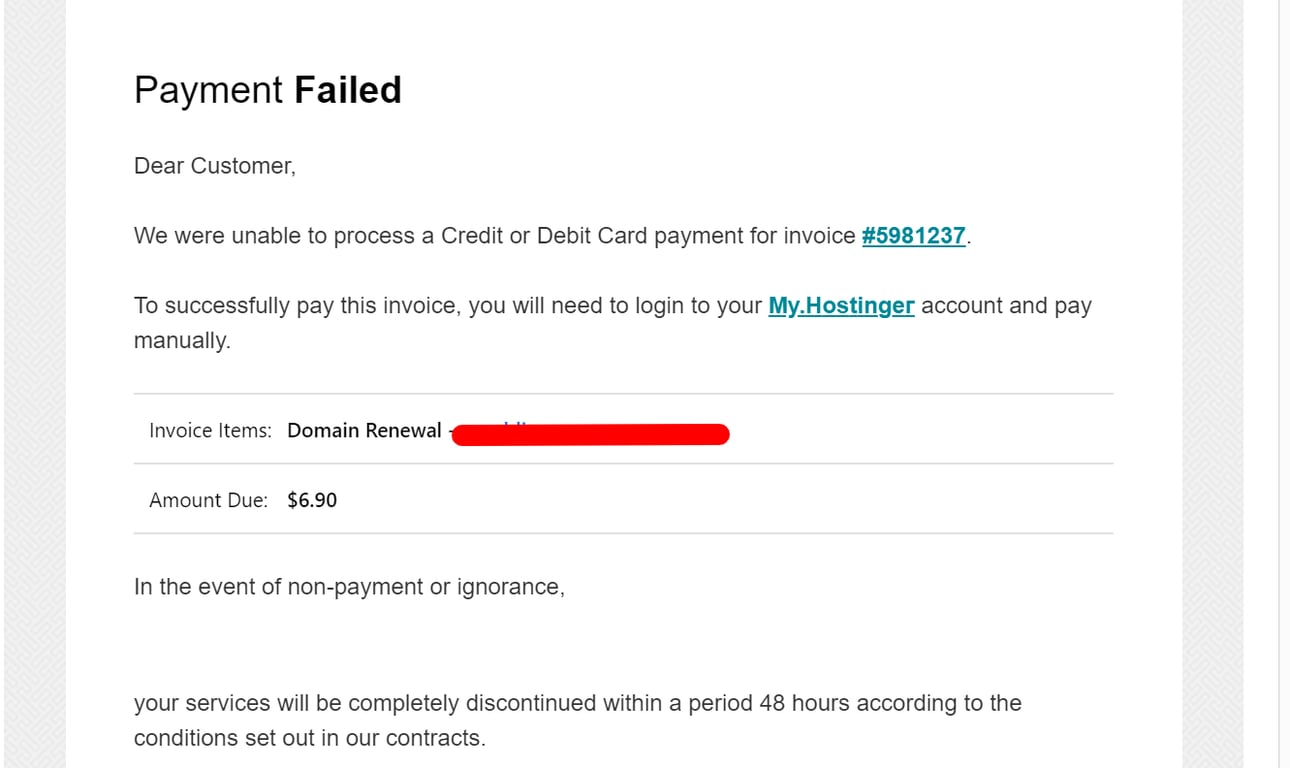
If you received this or a similar email, please, don’t click on any of the links, delete it, and report it to us.
How to spot a phishing attack?
Although we maintain controls to protect our networks and systems from cyber threats, we don’t have control of what scammers are sending to personal customer mailboxes which are not hosted on our servers.
In an effort to protect our customers, we want to highlight a common cyber-attack that everyone should be aware of – phishing.
“Phishing” is the most common type of cyber attack that affects organizations and individuals worldwide. Phishing attacks can take many forms, but they all share a common goal – getting you to share sensitive information such as login credentials, credit card information, or bank account details.
Types of phishing attacks to watch out for
- Phishing: In this type of attack, hackers impersonate a real company to obtain your login credentials. You may receive an email asking you to verify your account details with a link that takes you to an imposter login screen that delivers your information directly to the attackers.
- Spear Phishing: Spear phishing is a more sophisticated phishing attack that includes customized information that makes the attacker seem like a legitimate source. They may use your name and phone number and refer to a specific company in the email to trick you into thinking they have a connection to you, making you more likely to click a link or attachment that they provide.
- Shared Document Phishing: You may receive an email that appears to come from file-sharing sites like Dropbox or Google Drive alerting you that a document has been shared with you. The link provided in these emails will take you to a fake login page that mimics the real login page and will steal your account credentials.
What You Can Do
To avoid these phishing schemes, please observe the following email best practices:
- Do not click on links or attachments from senders that you do not recognize. Be especially wary of .zip or other compressed or executable file types.
- Do not provide sensitive personal information (like usernames and passwords) over email.
- Watch for email senders that use suspicious or misleading domain names.
- Inspect URLs carefully to make sure they’re legitimate and not imposter sites.
- Do not try to open any shared document that you’re not expecting to receive.
- If you can’t tell if an email is legitimate or not, reach out to company support directly via chat or contacts provided on their website. Never use contacts provided in the email.
- Be especially cautious when opening attachments or clicking links if you receive an email containing a warning banner indicating that it originated from an external source.
- Enable 2FA authentication on your accounts where possible.
If you have opened an email but didn’t click on anything, don’t worry then.
Contact customer support via Live Chat if you have any questions.




Comments
October 22 2023
Hope we have a good experience with hostinger.
December 06 2023
Hi there! We are committed to providing you with the best possible experience. If you have any questions or concerns, please do not hesitate to contact our Customer Success Team ?
October 20 2023
I am receiving Phishing Emails as described in your notice.
December 15 2023
Hi there! Thanks for letting us know. We're taking phishing very seriously. To confirm it's phising and ensure your safety, feel free to contact our Customer Success Team ?
October 06 2023
Why is it alright for others to attack. I dislike the term 'phishing'. Use 'Fishing' and us common people will connect to what is happening. We are the 'Fish' not the 'Phish' and this is not 'Catch and Release'. You need a weapon that will return in kind. Attack with Intent is a crime and should also be a crime on the internet. When there is a threat to the Scammer, the Scammer will have something to lose. Scammers today can lose NOTHING! It make me want to scam them. Can we? Please!
December 15 2023
Hello there! Thank you for sharing your concerns. We take online security seriously and continuously work to combat internet scams by improving security measures, educating users, and reporting scams to the appropriate authorities. Working together, we can create a safer online environment for everyone. If you encounter any suspicious activity, please report it to our Customer Success Team ?
April 18 2022
Gracias
April 15 2022
thank you